Gmail keeps popping up CAPTCHAs (reCAPTCHA or phone verification) during registration? It’s highly damaging to traffic conversion and multi-account scenarios. Many blame “Google’s over-sensitivity,” but it’s actually the result of multiple overlapping signals.
This article first clarifies the triggering mechanisms, then presents a set of legal and compliant practical strategies to significantly reduce the probability of challenges, and finally provides a summary and recommended tool references.
I. Why Gmail Registration Triggers Frequent CAPTCHAs
1. IP Reputation and Traffic Anomalies
If the number of requests from the same IP is abnormal (mass registrations/requests in a short time), Google will mark the IP as “suspicious,” triggering CAPTCHAs or the “Unusual traffic” page. Public proxies or certain data center IPs are more likely to be flagged.
If the same device/browser/network was previously associated with banned or abused accounts, new registrations will undergo stricter reviews. Similarly, residual traces of IPs with a “poor reputation” history increase the probability of challenges.
2. Abnormal Device Fingerprint and Browser Features
Inconsistencies or significant anomalies between browser fingerprints (User-Agent, Canvas, fonts, plugin fingerprints, etc.) and those of common real users raise the probability of being identified as automated. Frequent switching or using environments with obvious “automation characteristics” will be detected.
3. Phone/Verification History and Phone Pool Restrictions
Google has a limit on phone number usage: the same number used for multiple verifications will hit the limit. New numbers or certain virtual numbers have a higher rejection rate. Google may require SMS/voice verification as an “additional confirmation” method to prevent abuse.
4. Behavioral Patterns
Submitting forms in large quantities in an extremely short time, skipping page interactions, or lacking common interaction delays (mouse movements, typing rhythm) will make the system suspect automated scripts. Google’s detection associates these behaviors with account abuse.

II. Compliant “CAPTCHA Reduction” Complete Guide
1. Preparation: Build a “Trusted Environment”
(1) Select and Allocate IPs
Using the same IP or IP segment for mass registrations/logins in a short time will be deemed abnormal traffic by Google, prioritizing CAPTCHAs or phone verification. Common free proxies or data center IPs are more likely to appear on abuse blacklists or be marked by platforms as “non-home user traffic,” leading to stricter triggering policies.
Therefore, it’s recommended to assign an independent and region-consistent residential IP to each account, avoiding frequent IP switching.
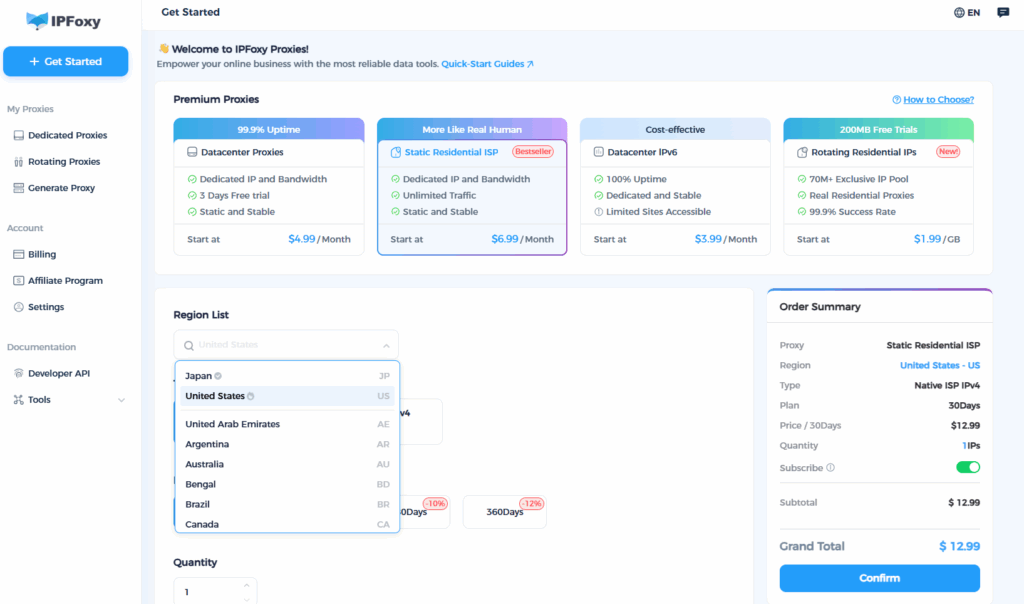
Practical Tip: If you need commercially scalable residential/mobile IPs, prioritize suppliers that offer sticky sessions, geographic coverage, and high-purity residential IPs.
- Its IPs come from real home or mobile networks, making them cleaner, more stable, and highly anonymous. They are closer to regular user traffic, reducing the probability of platform misjudgment.
- Supports session-level IP persistence, suitable for account nurturing scenarios, avoiding abnormal traces caused by frequent IP changes in a short time.
- Covers numerous countries, facilitating the allocation of region-consistent IPs based on target markets.
- Compatible with common fingerprint browsers or browser configuration management tools, integrating IP isolation and fingerprint isolation.
(2) Isolate Device Environments
Steps: Prepare an independent device environment for each account, ensuring UA, plugins, fonts, resolution, etc., are consistent with local users in the target country/region and remain unchanged.
Check: After launching the fingerprint browser, visit a browser fingerprint detection site to check for obvious “automation” signs in the fingerprint. The similarity should be within a reasonable range compared to real browsers in the same country.
(3) Prepare Phone Numbers and Verification Methods
Steps: Prepare real, long-term used mobile phone numbers (SIM cards) for registration. Preferably, they are phone numbers from the same country/region and have completed real-name authentication. Avoid one-time virtual numbers or low-reputation SMS platforms. It’s advisable to add a secondary email.
Check: The phone number can normally receive SMS/voice messages and has not been used multiple times in Google’s verification history.
2. Registration Execution
(1) Warm Up the Network and Browser Environment
Steps: On the fingerprint browser environment to be used, first open Google’s official website, search for several common keywords, log in or visit other websites to generate normal browsing traces.
Check: After warming up on the same IP/browser environment, accessing Gmail should not trigger an immediate CAPTCHA pop-up. If it does, cancel and switch to a different IP/browser.
(2) Decision-Making Process When Facing CAPTCHA/Phone Verification
If Google directly requests a phone number: Complete the verification with the prepared real phone number (prefer voice or acceptable SMS methods). Stop immediately after 2 failed verification attempts and switch to another phone number/IP to avoid repeated triggers.
If Google pops up reCAPTCHA: If the CAPTCHA fails or enters an infinite loop of challenges, terminate immediately, retry with a new IP, clear browser background cookies, or retry with a new browser.
3. Trust-Building Period for New Accounts
(1) Complete Basic Settings Immediately
Steps: After logging in, immediately upload an avatar, set a recovery email, enable 2FA (if compliant and available), and add some contacts/files. Avoid empty accounts.
Complete all basic settings within 48 hours, with no abnormal prompts on the account profile page.
(2) Low-Frequency Natural Usage
Steps: Perform a small number of real operations every day within the first 7 days: send 1–3 emails, open the inbox, watch 1 YouTube video, and visit Drive to upload/open 1 file. Do not immediately use it for large-scale outgoing or bulk actions.
Gradually increase usage frequency after the account stabilizes (7–14 days), but control the rate of adding new contacts/mass mailing behaviors. Conduct them in batches and spread them across different time periods.
It’s acceptable if no warnings or additional verification requirements appear within 72 hours after each increase in operations.
Summary
The root cause of frequent CAPTCHAs during Gmail registration is that the environment is deemed high-risk by the system due to anomalies. The core solution lies not in account registration tricks, but in building a stable, clean, and trusted registration environment.


